Finding Weak Active Directory Passwords
I recently worked with Thycotic to create a program called Weak Password Finder for Active Directory. The goal was to develop a tool that would be very easy to use yet powerful enough to yield actionable results. I think that this combination really makes it unique in the market. It basically does the same as my PowerShell module, but with a nice and shiny user interface:
It generates reports which are suitable for the management:
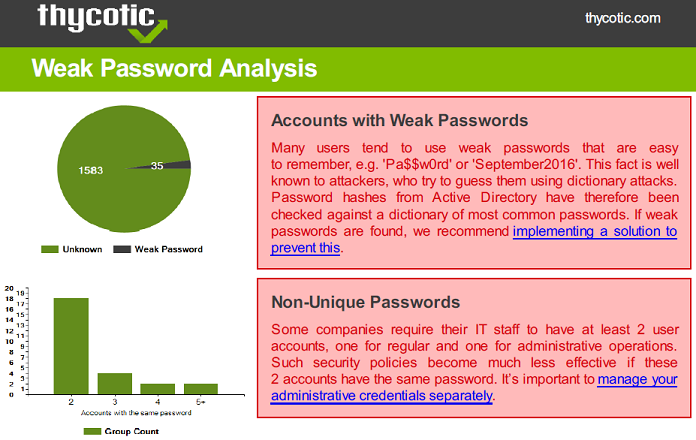
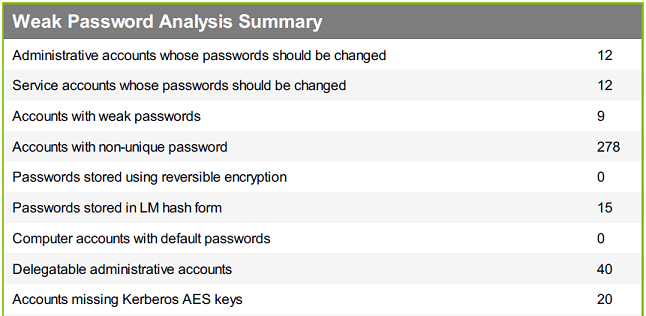
Of course, you can also drill down through the detailed data:
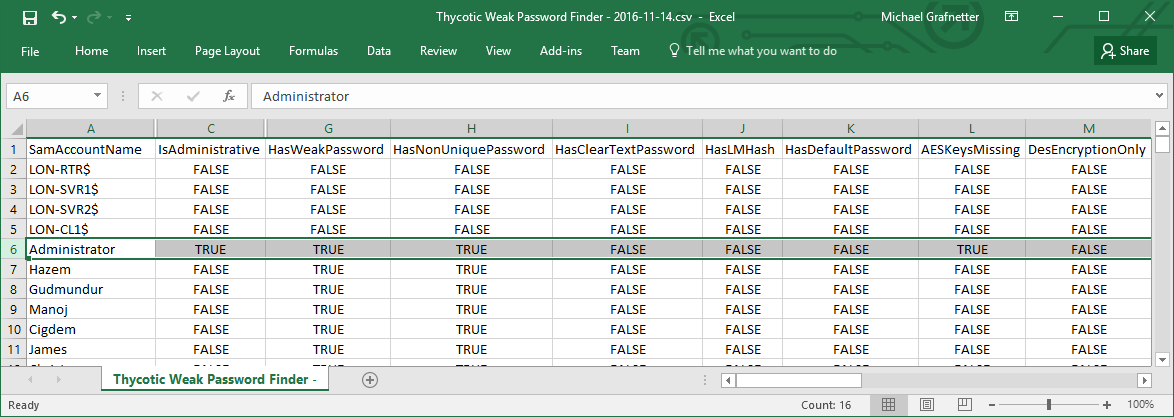
Here is a quick demo of the tool:
Did I mention that the Weak Password Finder is totally free?
 DSInternals
DSInternals