Dumping and Modifying Active Directory Database Using a Bootable Flash Drive
Since version 2.15, the DSInternals PowerShell Module fully supports Windows PE, the free minimalistic edition of Windows. This means that all the nasty Active Directory database stuff can now be performed from a bootable flash drive or an ISO image, including:
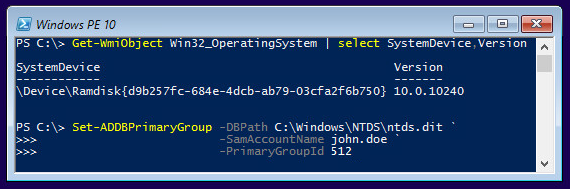
- Dumping NT hashes, kerberos keys and cleartext passwords from ntds.dit files.
- Modifying the SID History of user accounts and groups.
- Modifying the Primary Group ID of user accounts.
- Extracting the DPAPI domain backup keys.
DISCLAIMER: Features exposed through the DSInternals module are not supported by Microsoft and it is therefore not intended to be used in production environments. Improper use might cause irreversible damage to domain controllers or negatively impact domain security.
Required access
These actions would of course require an attacker to have one of the following:
- Physical access to a domain controller (DC).
- Knowledge of DC’s baseboard management controller (BMC) credentials.
- Administrative access to a virtualized DC.
In an ideal world, only Domain Admins should have such non-trivial access to the core AD infrastructure, but the everyday reality is far from perfect.
Creating the media
To create a bootable Windows PE media loaded with the DSInternals module, follow these steps:
- Install the Windows Assessment and Deployment Kit (ADK), including the Windows PE feature.
- Click Start, and type deployment. Right-click Deployment and Imaging Tools Environment and then select Run as administrator.
- Create a working copy of the Windows PE files. Specify either x86 or amd64:
copype amd64 C:\WinPE_amd64 - Mount the Windows PE image:
Dism /Mount-Image /ImageFile:"C:\WinPE_amd64\media\sources\boot.wim" /index:1 /MountDir:"C:\WinPE_amd64\mount" -
Add PowerShell support to Windows PE by adding a few optional components, together with their associated language packs:
Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\WinPE-WMI.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\en-us\WinPE-WMI_en-us.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\WinPE-NetFX.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\en-us\WinPE-NetFX_en-us.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\WinPE-Scripting.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\en-us\WinPE-Scripting_en-us.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\WinPE-PowerShell.cab" Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Program Files\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment\amd64\WinPE_OCs\en-us\WinPE-PowerShell_en-us.cab" -
Add the DSInternals PowerShell module to the Windows PE image by copying it into the C:\WinPE_amd64\mount\Windows\system32\ WindowsPowerShell\v1.0\Modules folder.
-
Add device drivers to the Windows PE image:
Dism /Add-Driver /Image:"C:\WinPE_amd64\mount" /Driver:"C:\DriversToEmbed" /Recurse -
Configure PowerShell to start automatically after boot by creating a file called winpeshl.ini in the C:\WinPE_amd64\mount\Windows\system32 folder, containing this text:
[LaunchApps] wpeinit.exe powershell.exe, -NoExit -NoLogo -ExecutionPolicy Bypass -
Create an ISO file containing the Windows PE files:
MakeWinPEMedia /ISO C:\WinPE_amd64 C:\WinPE_amd64\WinPE_amd64.isoThe same command can be used to create a bootable flash drive or VHD.
Final thoughts
As you have seen, it is pretty straightforward to create a bootable flash drive that can be used to conquer an Active Directory domain through a physically accessible DC. One of the precautions a domain administrator can take is to encrypt all DCs using BitLocker or other tool that does full volume encryption. Deploying RODCs at smaller branch offices is also a good idea. The new features in Windows Server 2016, Virtual TPMs and Shielded VMs, also seem very promising in regards to DC security.
 DSInternals
DSInternals